The Best of The Worst: "The 6 biggest ransomware attacks of the last 5 years"
Massive ransomware attacks are very much on the decline. But that's just part of story. Attacks are less widespread, instead successfully focused on high-revenue targets. Have you deployed essential enterprise-wide protections, including timely anti-malware updates, frequent data backups and multi-factor authentication? Don't be complacent or YOU will be a victim.
https://www.csoonline.com/article/3212260/the-5-biggest-ransomware-attacks-of-the-last-5-years.html
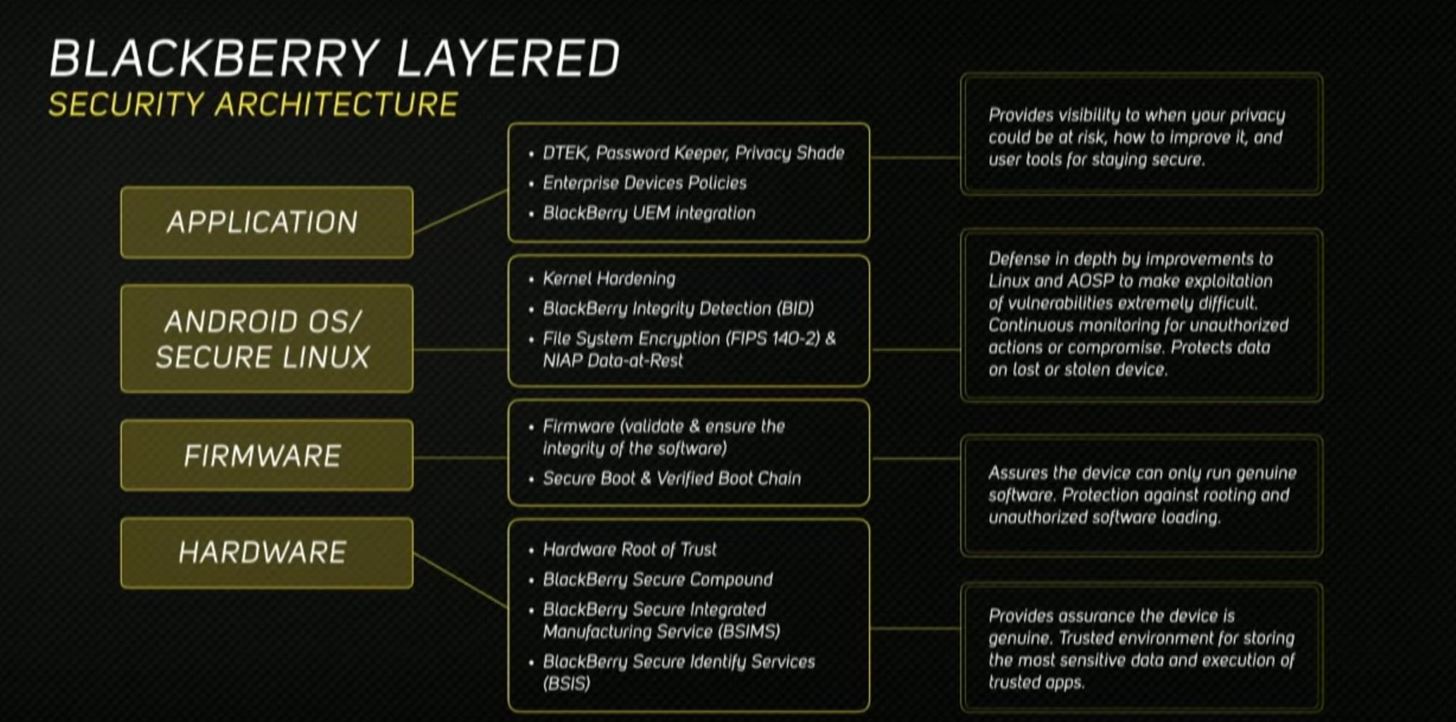
Is the Blackberry (and keypad) back from the dead?
Read about its slick hardware/OS security features including a hardened Linux kernel, no root access and my favorite: real-time, customizable monitoring for apps accessing camera, your location and more.
For your business, awareness is essential to data security. At Trestle Networks, our Insight Monitoring solution provides every customer that 24x7 view into mission-critical infrastructure, key to rapid response.
Contact me to learn more and subscribe to trestleNEWS at www.trestlenetworks.com to read these daily posts.
COSCO?? Oh, not "COSTCO".
But a high-impact ransomware attack against the world 4th largest shipper is big news too.
And this chuckle-worthy quote from the story: "Internal emails suggest the firm has been hit by ransomware in the US and is asking staff not to open suspicious emails." (Sigh) The vast, vast majority of attacks are not kind of "Mission Impossible"-style operation. Attackers play on carelessness. Are you protected when your employees click on the wrong link?
At Trestle Networks, we work closely with our Managed Security and Managed WiFi (powered by Mojo Networks) customers to protect your mission-critical systems, while 24x7 monitoring all infrastructure.
Contact me to learn more and visit trestleNEWS at www.trestlenetworks.com today to see these daily posts.
"Evil Twins" and other airport dangers
Free WiFi is super tempting, especially with a safe-sounding SSID like "SouthwestWiFi". Don't be a victim of "Evil Twins" at airports (or, really, anywhere). Oh, and make sure your devices NEVER automatically connect to any SSID...
At Trestle Networks, our Managed WiFi customers are protected 24x7 by Mojo Networks' patented WIPS, including "Evil Twin" detection and disruption. How about you?
Contact me to learn more and visit trestleNEWS at www.trestlenetworks.com today to see these daily posts.
Bluetooth and Man-in-the-Middle
Heard about the latest Bluetooth pairing vulnerability (it's all about poor public key validation) that's forcing fixes for Apple, Broadcom, Dell and other laptops using Qualcomm’s Bluetooth chips? The risk isn't huge, but get ready patch your Bluetooth-enabled devices soon...
At Trestle Networks, we work closely with our Managed Security and Managed WiFi (powered by Mojo Networks) customers to quickly patch vulnerable code, while 24x7 monitoring their infrastructure against potential attacks and ensuring PCI DSS v3.2 compliance. Contact me to learn more and visit trestleNEWS at www.trestlenetworks.com today to see these daily posts.
802.1ax is coming...
...but will it be a WiFi difference-maker? Or is it chock full of powerful features with limited real-world use? Check out this great blog post by our trusted partner Mojo Networks, describing 802.1ax's key features, including uplink MU-MIMO, a big upgrade over 802.1ac's downlink MU-MIMO only. And like for 802.11ac, don't rush to get your business the first shiny 802.1ax APs. Get guidance from pros before you take the leap.
At Trestle Networks, we work with our Mojo-powered Managed WiFi customers to always fit the right APs at the right time to their unique needs. Contact me to learn more and sign up for trestleNEWS to receive these daily posts.
Don't End Up Like Under Armour
Could a data breach get your business facing a potential class action lawsuit?
That's exactly where Under Armour is now. Read about how this ubiquitous brand exposed usernames and email addresses of MyFitnessPal users. And potentially much, much more.
At Trestle Networks, our Managed Security and Managed WiFi solutions secure each customer's infrastructure, delivering PCI compliance and 24x7 protection against disastrous data breaches. Contact me to learn more and visit trestleNEWS at www.trestlenetworks.com to see these daily posts.
Protect Your Business (From Those You Trust).
Read all about the September 2017 data breach that hit Coca-Cola, exposing 8,000 employees' personal data. How'd it happen? A former employee simply walked out the door with an external hard drive.
Q: Do you take the security of your physical assets and data more seriously than Coke did?
Sure hope so.
At Trestle Networks, we work closely with our Managed Security and Managed WiFi (powered by Mojo Networks) customers to secure their infrastructure and lockdown access to sensitive data, while ensuring 24x7 PCI DSS 3.2 compliance. Contact me to learn more and visit www.trestlenetworks.com today.
Do You Have WiFi Superpowers?
In the minds of your corporate and guest WiFi users, are you an IT superhero? Or are you the villain? Check this fun animation by our trusted partner, Mojo Networks. With the power of Cognitive WiFi in your hands, you're definitely going to save the day!
At Trestle Networks, we work closely with our Managed WiFi (powered by Mojo Networks, Inc.) customers to deliver top performance, powerful analytics and industry-best security. Contact me to learn more and visit trestleNEWS at www.trestlenetworks.com to see these daily posts.
Goodbye, Apple Airports
I missed this bittersweet WiFi news last month. Apple is officially discontinuing its Airport base stations. My long-since home office Airport Express -- replaced by amazing Mojo Networks' C-130 tri-radio access points -- now lives on as a handy little RF beacon when performing WiFi site surveys.
Speaking of moving on... Is your enterprise WiFi way overdue for an overhaul? At Trestle Networks, we work with our Managed WiFi (powered by Mojo Networks) customers to deliver top performance, powerful analytics and industry-best security. Contact us to learn more and visit trestleNEWS to see these daily posts.
When Mantis Attack
How vulnerable are your business' mobile and desktop devices? Read all about the Roaming Mantis malware that's using compromised routers and DNS hijacking to launch sophisticated phishing attacks on users, smartphone crypto mining and worse.
At Trestle Networks, we work together with our Managed Security and Managed WiFi (powered by Mojo Networks) customers to secure their infrastructure, reducing vulnerability to compromise and attacks like Roaming Mantis. Contact us to learn more and subscribe to trestleNEWS to see these daily posts.
Don't Get Doppelganged. It's Expensive.
Have your heard about this particularly nasty ransomware, SynAck, that relies on the awesomely named "Process Doppelgänging technique"? It's sneaky. It's expensive ($3,000 to decrypt your system) when you're infected. It's one more reminder to properly protect your business.
At Trestle Networks, we work together with our Managed Security and Managed WiFi (powered by Mojo Networks) customers to secure their infrastructure and address known security vulnerabilities, including ransomware. Contact me to learn more and subscribe to trestleNEWS to see these daily posts.
Like Bob Slydell in "Office Space"... they fixed the glitch.
Read about this security screw-up by Twitter that potentially exposed -- thankfully only in an internal log -- the plaintext passwords of 330 million users.
Were you prompted by Twitter tonight to change your password? While you're at it, be sure to enable multi-factor authentication too, if you haven't already.
At Trestle Networks, we work closely with our Managed Security and Managed WiFi (powered by Mojo Networks) customers to be secure their credentials and enforce multi-factor authentication, a PCI DSS 3.2 requirement. Contact me to learn more and subscribe to trestleNEWS to see these daily posts.
IoIT (Internet of Insecure Things)
The key quote from this article: “A lot of the manufacturing behind IoT devices today feels like the Gold Rush… everyone wants to get there in a hurry,”
When you're in a hurry, sloppy cybersecurity is painfully easy, making #IoT risks very real, thanks to weak (sometimes hard-coded) default credentials and wide-open Internet access.
Will your IoT devices become solidiers in the next Mirai-style botnet attack?
At Trestle Networks, we work closely with our Managed Security and Managed WiFi (powered by Mojo Networks) customers to 24x7 monitor and protect their infrastructure against both external attacks. Contact me to learn more and subscribe to trestleNEWS to receive these daily posts.
Touch Without Touch
You hands are wet. You try to unlock your phone via fingerprint on the home button. FAIL. That's an annoying downside of capacitive scanner technology (on top of spreading germs via touch sensors shared among multiple users).
In what could be a future replacement, read about a French company's new touchless authentication sensor that relies on 3D modeling.
Whether hit-or-miss finger scanners, bleeding-edge tech or trusted OTP, make MFA (multi-factor authentication) mandatory for controlling user access to your critical business systems.
The world's biggest known DDoS attack... so far.
Peaking at 1.35Tbps, the pounding of GitHub was truly massive, at more than 2x the peak traffic rate of 2016's Mirai attack. That said, GitHub did a solid job at incident response, including quickly shifting all their traffic Akamai, then dropping the hammer on a several bad traffic sources.
How ready is your business infrastructure -- from distributed SMBs to large data center environments -- for the next attack? Also, how will you respond if your critical SaaS apps are impacted, like a Dyn DNS-style outage?
AI and Eyes
Are eyes the windows into your soul? Very deep and possibly true... But they may also be vital tools in your health monitoring. See what Alphabet's Google and Verify Life Sciences are detecting via a deep-learning algorithm and your retinas.
AI-driven analysis of the spiderweb of retina blood vessels is helping detect abnormally high cholesterol levels, elevated blood pressure and more.
Like image recognition, enterprise-class security monitoring is about knowing what to look for, quick identification of those abnormalities and rapid response.
Intel and 32 Lawsuits
While Intel’s Spectre and Meltdown security flaws were the bloodiest of black eyes, the tech titan’s response has been that much worse.
Patches that none other than Linus Torvalds called “insane” and did more harm than good...
Suspicion of insider trading in advance of their public announcement of the flaws...
When your business is hit with a major security incident (self-inflicted or not), will you respond better than Intel? Do you have the right people and processes in place, ready to take action? For starters, at least don't dig yourself a deeper hole.
Casually Bypassing TSA...
A quick thought on my trip this morning through Denver's TSA "security theater".
Have you seen this happen? A male traveler was stopped upon exit from our line's full-body scanner. For whatever reason, he then received a pat down and other attention from multiple TSA officers. In response to the line delay, another officer waived at least 6 other travelers -- including myself -- through the old-school metal detectors instead, skipping both a full-body pat down or scan ("deep inspection").
This (I hope) non-malicious "denial of service" triggered a casual bypass of TSA's perimeter security, simply keep the line moving. Wondering how many times this happens daily at airports, coast-to-coast? Might bad actors take advantage of this bypass, use it as a "smoke screen" for their real attacks? Oh boy...safe travels...
In your business, are you guilty of cutting security corners to complete a project, quickly close a ticket or simply get network traffic moving?
When A Gap Isn't a Gap...
You believed air gaps and Faraday cages are bulletproof ways to isolate sensitive systems and data from attackers?
Wrong. Read all about the attacks documented by Ben-Gurion University -- one awesomely named "Magneto" -- that exploit the low-frequency magnetic radiation of CPUs to transfer data.
The Geek Factor is sky high with this one. I want to validate it in my under-construction Faraday cage pictured below (hardware courtesy of Home Depot).
Are your business systems and mission-critical data as secure as you think?